A new research report by Checkpoint has disclosed a bug present in the Instagram App that can be used by hackers to exploit the consumers.
The photo/video sharing app has over 1 billion users worldwide and the bug within the app was identified by the security researchers at Checkpoint earlier this year.A recent report also suggested that Facebook was using Instagram to spy on its users.
Read More: Facebook accused of watching Instagram users through camera: Report
If these are the kind of bugs or vulnerabilities that an app, such as Instagram has, the main question that arises here is whether the social media application is still safe to use?
The critical vulnerability would have given an attacker the ability to take over a victim’s Instagram account into a spying tool, simply by sending them a malicious image file. When the image is saved and opened in the Instagram app, the exploit would give the hacker full access to the victim’s Instagram messages and images, allowing them to post or delete images at will, as well as giving access to the phone’s contacts, camera and location data.
This type of bug shouldn’t have been present in the app in the first place, but even if it is there, the one thing that allows the hackers to exploit users in such a way is the permissions an app asks you to grant.
For example, a map application should be able to access your location, but should not have access to your microphone; a dating app should be able to access your camera and nothing else, and so on. An app like Instagram here, has almost all the permissions that are required by a hacker to hack a certain device.
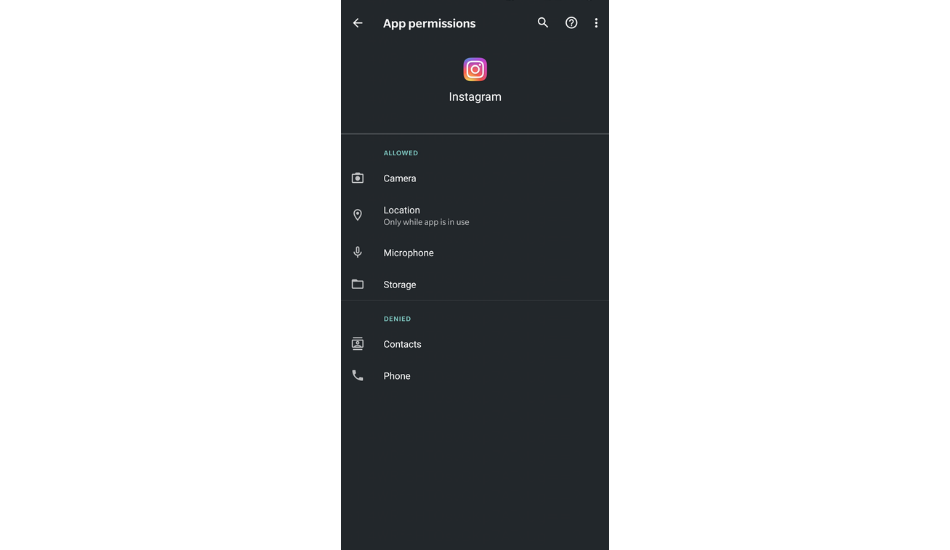
If your Instagram app is hacked, the hacker will have easy access to your GPS data, camera, microphone, contacts, and more.
The research by Check Point revealed the critical vulnerability that might allow the attackers to remotely execute the malicious code into your phone. It is technically referred to as – remote code execution (RCE). This vulnerability can allow an attacker to perform any action they wish in the Instagram app (even if it is not actually a part of the application logic or features). Since the Instagram app has very extensive permissions which are required for it to work without any issues, it may allow an attacker to instantly turn the targeted phone into a perfect spying tool which in turn puts the privacy of millions of users at serious risk.
The culprit behind the vulnerability was Mozjpeg, which is an open-source project used by Instagram as its JPEG format image decoder for images uploaded to the service. Instagram relies on 3rd party libraries like these to handle the common jobs of an app, like image processing. This way, the developer’s job is less burden than what it already is.
The resources that could be accessed by the hacker after your device has been hacked includes but are not limited to, contacts, device storage, location services and the device camera. The basic problem the hack could cause is the crash of the Instagram app, which would not be resolved unless the user re-installs the app.
Fortunately, the findings were reported to Facebook and the Instagram team, to which the companies replied that they will be issuing a patch on the newer version of the application, on every platform Instagram is available on.
The patch for this was already released 6 months ago by Facebook and Instagram which would have allowed every user to update the app by now. If you are not on the latest version of the app, we strongly suggest you to update it from the Play Store / App Store or whatever store is available on your platform.


