1Which apps did get removed from the Google Play Store?
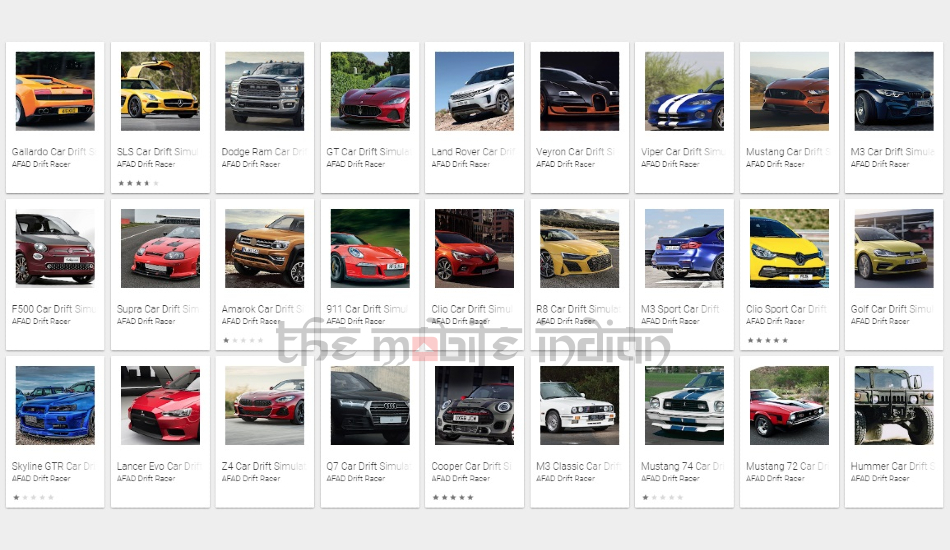
Google removed a total of 27 apps from the Play Store and as mentioned by Quickheal, the links to the malicious apps have now been removed by Google. As we list these links down below, we note that none of the links will work since all apps have now been removed.
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.cliosport
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.veyron
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.sls
https[:]//play[.]google[.]com/apps/details?id=com.cit.dodgeram
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.gt
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.gallardo
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.mustang
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.supra
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.viper
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.m3
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.f500
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.p911
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.amarok
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.mustang72
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.mustang74
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.q7
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.m3classic
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.gam
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.r8
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.skylinegtr
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.m3sport
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.golf
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.clio
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.gam
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.cooper
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.lancerevo
https[:]//play[.]google[.]com/store/apps/details?id=com.cit.hummer&hl=en
2How were these malicious apps targetted?

It has been found that all the 27 apps reported to be malicious were published by the same developer with the name “AFAD Drift Racer”. The apps carry a logo and name that resemble that of a racing car game and were easily found under the free Car Racing Games category on the original Google Play Store.
3How the malicious apps installed a Fake Play Store?
If a user installed any one of the above-mentioned apps, they were repeatedly greeted by an installation prompt of a fake Google Play Store. The fake store disguises itself as a pre-requirement for the installed game to run.
4Do games need more apps in order to work?

In reality, the Google Play Games is what handles all the games that are listed on the Play Store. The original Google Play Games doesn’t get download by itself, either does it serve repeated popups for installation. If any game is not supported by the latest version of Google Play Games, then there is a pop-up to update Google Play Games which redirects users to the Google play store.
5What makes the fake Google Play Store look almost genuine?

To create an illusion that the user was installing the genuine Google Play Store app, the fake store used a similar icon which looks a lot like the Google Play Store icon or that of a previous version of the Play Store. To give no room for users to find out that they committed a mistake, the fake Google Play Store App would get hidden from the launcher while running in the background.
6How does the process of installing the Adware take place?

After installing and opening one of the 27 apps listed, users were continuously shown an installation prompt of fake Google Play Store. Even if they cancel the installation prompt, a pop-up would keep appearing until the user installed the app.
7What all permissions does the fake Google Play Store ask for?
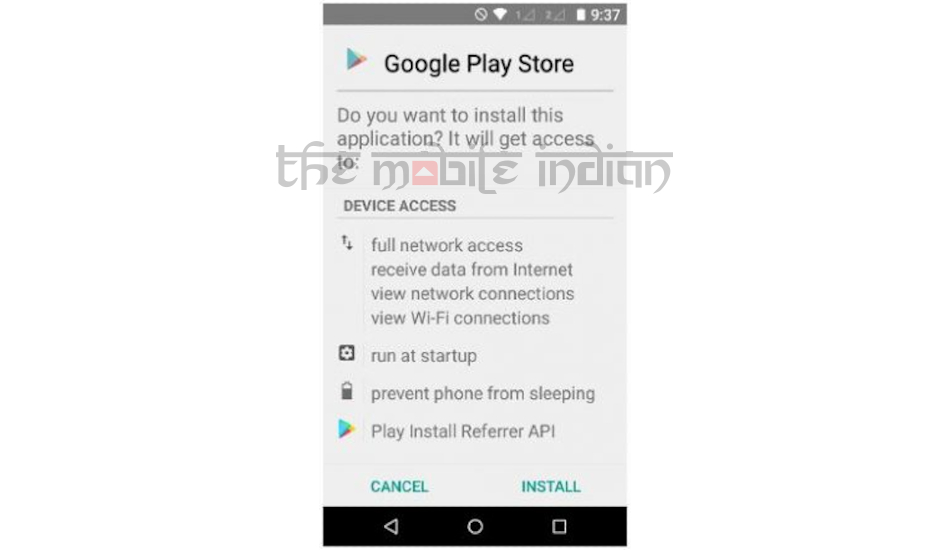
Right off the bat, the fake Store app demands that a user assign full network access and the ability to view all networks connections and WiFi. This means the app would keep using your metered data connection to loot your data limit and also keep it switched on till the phone is switched off. The fake store also additionally request that the use allow the app from preventing the phone from sleeping and run the app on boot. This means the app will consume all the resources to stay up even when the phone is idle and will drain the battery even when a person isn’t using the phone.
8What kind of a malicious app is it and what does it do?
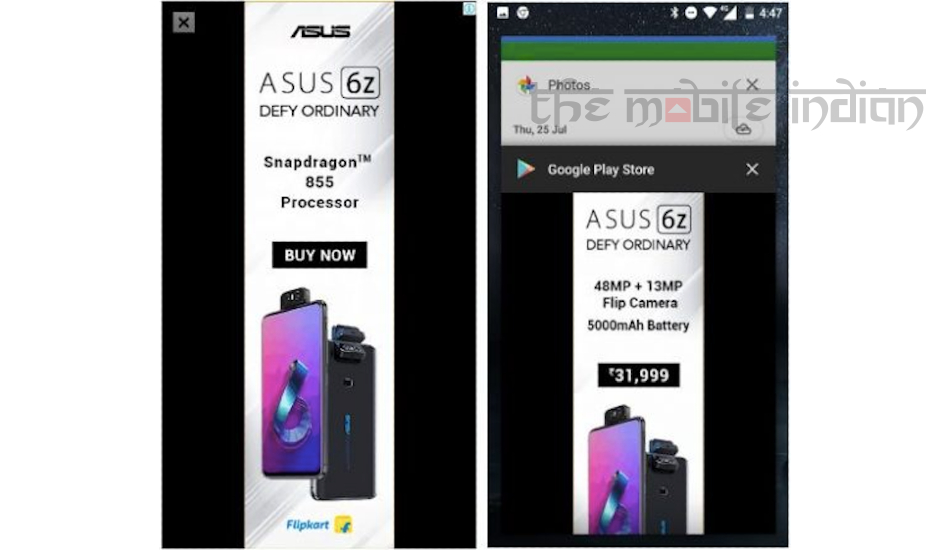
Quick Heal has named the Fake Play Store into the “Android.Dropper.F” category because on executing the parent app, it launches the dropped app. The dropped app keeps on running in the background and shows full-screen ads till you don’t uninstall it manually. Malware authors can run aggressive ads and make money while the user fumes and wastes their time by searching for what’s wrong in their device.
9How to check and remove if a fake Play Store is installed on your phone?
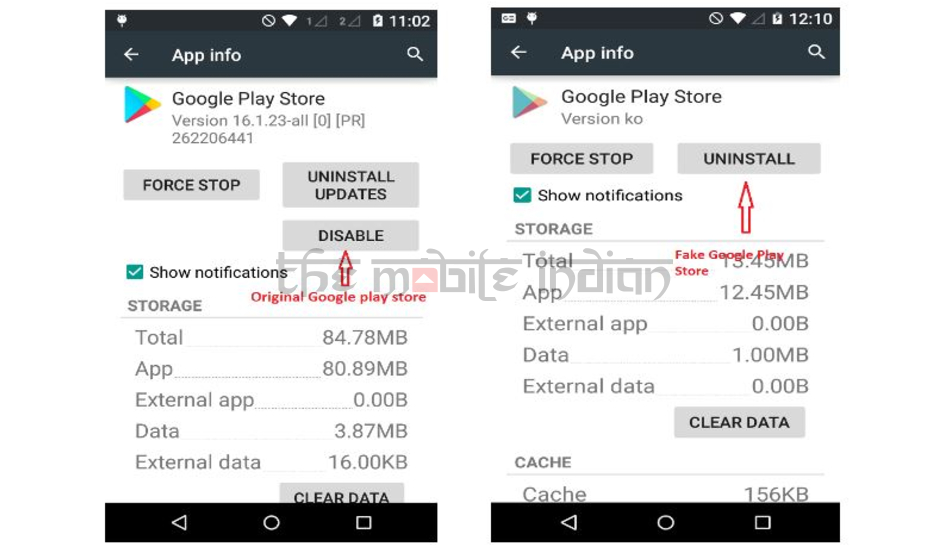
1. Head over to Settings > Apps (Apps & notifications / App Manager).
2. Identify the fake Play Store from the Original Play Store. It’s important to note that the Genuine Google Play Store cannot be uninstalled and can only be disabled.
3. If you found the fake Play Store with an option to uninstall, then uninstall the app as soon as you can and also uninstall the original app that prompted you to install the fake store in the first place.
10How to stay protected from fake mobile apps?

1. Read an app’s description before downloading and installing.
2. Check if the app developer is verified and has a genuine website to contact in case of emergencies.
3. Go through the app’s reviews and ratings which will give you a basic idea of whether the app can be reliable or not.
4. Do not download apps from third-party app stores which can contain even more malicious apps than what’s available on the Play Store.
5. Install a reliable mobile antivirus app which can prevent fake and malicious apps from getting installed on a phone.


