The increase in the number of applications that have come up on the Android marketplace has opened up newer avenues for developers to ear and present content to the Android community. But the dark side of the fact is that the rise in the number of applications has also opened up opportunities for cyber criminals to invent newer ways to catch hold of confidential user data.
According to the newest security threat that has been identified for Android users, the Trojan or a malicious program disguised as an application has found out to be recording conversations that users do using their smartphones.
There are a couple of developers who try to fool people with their applications that claim to provide seamless messenger connectivity between devices such as iPhones and BlackBerrys. Many people fall for this as the application sounds promising and fulfils the need for connectivity with friends handing different devices.
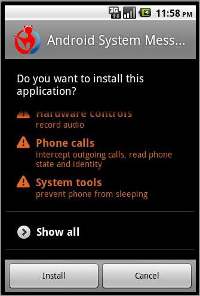 The CA security advisor research blog found out a similar application infected with a Trojan. Upon testing, it was found out that once the application is installed on the device, the Trojan activates itself and records ever conversation that takes place on the device in a low quality audio format so that the user does not even have a clue about it.
The CA security advisor research blog found out a similar application infected with a Trojan. Upon testing, it was found out that once the application is installed on the device, the Trojan activates itself and records ever conversation that takes place on the device in a low quality audio format so that the user does not even have a clue about it.
After the call is complete the Trojan then can easily send the file through an email to any email address as an attachment, making your private conversation open.
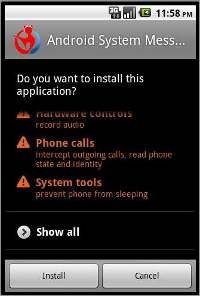
Android as an operating system is secure in itself as it asks or prompts the user every time an application is being installed on the device. But as a practice many users do not see the permissions that the application asks for and allows it to install on the device.
So if you are an Android user, make it a regular practice to carefully go through the permissions or access conditions that application is seeking for. And if anything seems suspicious the user should avoid installing the application.